Demilitarized zone dmz. DMZ - what is it in the router? DMZ and video surveillance. Virtual DMZ server on Tenda router
In our article we will examine the concept of DMZ in detail. We will try to answer questions about what a DMZ is, how it came about, and how to set up a DMZ. Everyone can learn for themselves at least general information on this topic.
Reasons for the emergence of demilitarized zones
Nowadays it is less and less common to find any companies without computers. And where there are computers, there is also an internal local network that connects them together.
The mere presence of a common internal local network- it is very practical and safe. But with the advent of the World Wide Web, everything became a little more complicated. Nowadays, the vast majority of companies use the services of the World Wide Web. This greatly simplifies the work process, since everyone can find any information they are interested in in a matter of seconds.
But with the development of the Internet, the threat of penetration into the company’s general local network from the outside also appeared. First of all, this concerned companies with public Internet services available to any user of the World Wide Web. The danger was that an attacker, having gained access to a web service, could also gain access to personal information, stored on any of the computers connected to the internal local network. This has caused a number of difficulties that are resolved by creating a DMZ.
Original source
The first thing to know about the DMZ is that it is primarily a military term, originating from the designation "demilitarized zone." It means a certain area of territory located between two warring states. It prohibits any form of military activity - be it a special operation, sabotage or espionage.
Demilitarized Zone DMZ: Architecture and Implementation
From the interpretation of the original term, it becomes clear to us that a DMZ is a certain area of terrain in which any type of harmful activity is prohibited. And this extremely successfully characterizes the whole essence of this, let’s say, trick.
What we should understand about the DMZ concept itself is that it is an extremely simple solution, which is the creation of a separate segment computer network, isolated from all external Internet hosting and from the company’s internal network. It is also a restriction of control or a complete ban on access to both the Internet and the internal network.

Creating a separate network segment is quite easy. For this, firewalls or firewalls are used. The average user may be familiar with the word “firewall” from films about famous hackers, but few people know what it is.
A firewall is a software and hardware unit of a computer network that divides it into sectors and allows you to filter incoming network traffic according to the rules specified by the operator (administrator). Also, in the event of unauthorized entry, the attacker gains access only to those files that are located within the separated sector, without damaging the rest.

There are at least two types of demilitarized zone configurations - with one firewall or with many. In the first configuration, the firewall divides the network into three sectors:
- internal network;
- Internet channel.
However, this method still provides an insufficient level of protection. Most large companies still use the second method - with big amount firewalls. In this case, the attacker will have to overcome at least one additional system perimeter with its own traffic filter, which significantly increases security.
Settings
We are sure that many have already become sufficiently aware of DMZ, that it is a simple and effective way to ensure the security of your computer network. Users of multi-channel Internet routers can judge for themselves this ingenious trick for hackers.
All that is required to set up DMZ is to display one device as a local network, connecting it via a separate cord to a free socket on the router, then assigning it a static IP address, then activating it in the DMZ window and restarting the device.
Before any manipulations, you should make sure that all devices have latest versions protection. After that, you can freely use this simple but effective protection against attacks on your personal data.
This article summarized all the most important facts about DMZ: what it is, how it works, and, most importantly, its purpose.
Description
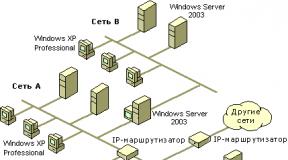
A demilitarized zone or DMZ is a network segment with white-label addressing, separated by a firewall from the Internet and the organization’s local network. Servers that need to be accessible from the Internet, such as a mail or web server, are usually placed in a DMZ. Since servers in the DMZ network are separated from the local network by a firewall, if they are hacked, an attacker will not be able to gain access to local network resources.
Settings
The demilitarized zone is created in the “providers and networks” module. When creating it, you must specify the IP address of the Internet Control Server and the DMZ network mask, and also select the network interface for the DMZ. For security reasons, a separate network interface is usually used for the DMZ.

By default, servers located in the DMZ do not have access to the Internet and local network, so access for them must be configured using rules firewall.
The “NAT from local networks” checkbox allows you to control the translation of local addresses to the DMZ network. By default it is disabled, i.e. The NAT service for the DMZ network interface does not work, addresses are translated without changes.
Important: Actually NAT for the DMZ network on external interfaces The ICS is disabled, so “white” IP addresses must be used to address it. Setting up a DMZ network makes sense if you need to control external access to servers on the local network that have “white” IP addresses. In all other cases, a regular local network is configured.
In the era of cloud computing, DMZ (Demilitarized Zone, demilitarized zone, DMZ is a physical or logical network segment that contains and provides public services to an organization, and also separates them from other sections of the local network, which allows for internal information space additional protection from external attacks) has become much more important—and at the same time more vulnerable—than its original architects ever imagined.
Ten or twenty years ago, when most endpoints were still on a company's internal network, a DMZ was just an extension to the network. Users outside the local computer network, very rarely requested access to internal services, and vice versa, the need for access local users access to public services also did not arise often, so at that time the DMZ did little to provide information security. What happened to her role now?

Today you are either a software company, or you work with a huge number of SaaS service providers (Software as a service, software as a service). One way or another, you constantly have to provide access to users located outside of your LAN, or request access to services located in the cloud. As a result, your DMZ is filled to capacity with various applications. And although the DMZ, as originally intended, should serve as a kind of control point your perimeter, these days its function increasingly resembles an external advertising sign for cybercriminals.
Every service you run in the DMZ is another information message to potential hackers about how many users you have, where you store your critical business information, and whether that data contains anything an attacker might want to steal. Below are four best practics, which will allow you to enable and configure DMZ so that you can stop all this mess.

1. Make the DMZ a truly separate network segment
The basic idea behind a DMZ is that it should be truly separate from the rest of the LAN. Therefore, you need to enable different IP routing and security policies for the DMZ and the rest of your internal network. This will make life much more difficult for the cybercriminals who attack you, because even if they understand your DMZ, they will not be able to use this knowledge to attack your LAN.
2. Configure services inside and outside the DMZ zone
Ideally, all services that are outside of your DMZ should install direct connection only to the DMZ zone itself. Services located inside the DMZ should only connect to the outside world through proxy servers. Services located inside the DMZ are more secure than those located outside it. Services that are better protected should take on the role of the client when making requests from less secure areas.
3. Use two firewalls to access the DMZ
Although it is possible to enable DMZ using only one firewall with three or more network interfaces A setup that uses two firewalls will give you a stronger means of deterring cybercriminals. The first firewall is used on the outer perimeter and serves only to direct traffic exclusively to the DMZ. The second, the internal firewall, handles traffic from the DMZ to the internal network. This approach is considered more secure because it creates two separate, independent obstacles in the path of a hacker who decides to attack your network.
4. Implement Reverse Access technology

Safe-T's Reverse Access technology will make the DMZ even more secure. This dual-server technology eliminates the need to open any ports on the firewall, while at the same time providing secure access to applications across networks (via a firewall). The solution includes:
- External server - installed in the DMZ / external / unprotected network segment.
- Internal server - installed in the internal/protected network segment.
The role of the external server, located in the organization's DMZ (on-site or in the cloud), is to maintain the client side of the user interface (front-end) to various services and applications located on the World Wide Web. It operates without the need to open any ports on the internal firewall and ensures that only legitimate session data can enter the internal LAN. An external server performs TCP offload, allowing you to support any TCP-based application without the need to decrypt cryptographic traffic data SSL protocol(Secure Sockets Layer, level of secure sockets).
Role internal server is to push session data into the internal network from an external SDA (Software-Defined Access) node, and, if the session is legitimate, perform Layer 7 proxy functionality (SSL offloading, URL rewriting , DPI (Deep Packet Inspection, detailed packet analysis), etc.) and pass it to the addressed application server.
Reverse Access technology allows you to authenticate users' access permission before they can access your mission-critical applications. An attacker who gains access to your applications through a rogue session could probe your network, attempt code injection attacks, or even move around your network. But without the ability to position their session as legitimate, the attacker who attacks you loses most of his tools, becoming significantly more limited in resources.

Eternal paranoid, Anton Kochukov.
Owners of home Wi-Fi routers may sometimes encounter the fact that some programs or games operate with restrictions. In some cases, it is advisable to use forwarding in the router. There are several redirection methods, each of which has some advantages and disadvantages. One of these is DMZ. Most models network devices This item is present in the parameters, but not everyone knows what it is and what to use it for. If you don't know either, this information is for you.
Most ordinary users have not even heard of DMZ technology
What is DMZ
It is a physical or virtual server that serves as a buffer between the local network and the Internet. Used to provide local network users with services Email, remote servers, web applications and other programs that require access to the World Wide Web. To access internal resources from the outside, you need to go through the authorization procedure; an attempt to log in for unauthorized users will not be successful. In most cases this is a router setting.
The name comes from the English acronym denoting the demilitarized zone as a barrier between warring territories. This technology is used when you create a home server that must be accessed from any computer connected to the Internet. A true demilitarized zone is used in large corporate networks with high levels of internal protection. Home router models completely open the computer to access the Internet.

When is DMZ used?
Considering the openness of the computer, the method is considered quite dangerous, so it is worth using it when other redirection methods do not give the desired result.
- For applications that require the opening of all available ports. There are few of them, but they do occur.
- Hosting home server. Sometimes you need to host a shared resource at home, so this setting will be indispensable for separating the server from the local network.
- Use of game consoles. In most moments automatic setting Router redirection allows you to use consoles to play online without additional manipulations. But in some cases, only DMZ will give the desired effect.

Setting up DMZ in the router
For DMZ to work successfully on your network, your router must be configured correctly. It's absolutely not difficult. Log in to settings via the web interface. Typically, the IP address, login and login password are indicated on the router itself or in its instructions. Depending on the manufacturer, this section may be located either in the “Internet Settings” or “Forwarding” tab.
- The first step in the DHCP server settings is to assign a static one on which the server will be organized;
- After that, in the DMZ tab, activate the “Enable” item and add the assigned IP address, save and reboot the device;
- Make sure that all devices on your network have the latest security updates installed, as while convenient, they are subject to additional risks.
Conclusion
Now you know what a DMZ is and how it is configured. Usually there is practically no need to use it at home.
Do you use this technology on your router? For what purpose? We invite you to leave comments.
DMZ or Demilitarized Zone (DMZ) is a network security technology in which servers responding to requests from an external network are located in a special network segment and are limited in access to main network segments using firewall (firewall), in order to minimize damage during the hacking of one of the services located in the zone.
Single firewall configuration
Scheme with one firewall
In this scheme DMZ the internal network and external network are connected to different ports of the router (acting as a firewall), which controls connections between networks. This scheme is easy to implement and requires only one additional port. However, if the router is hacked (or configured incorrectly), the network becomes vulnerable directly from the external network.
Dual firewall configuration
In configuration with 2 DMZ firewalls connects to two routers, one of which limits connections from the external network to DMZ, and the second controls connections from DMZ to the internal network. This scheme allows you to minimize the consequences of hacking any of the firewalls or servers interacting with the external network - until the internal firewall is hacked, the attacker will not have arbitrary access to the internal network.

Three firewall configuration
There is a rare configuration with 3 firewalls. In this configuration, the first of them accepts requests from the external network, the second controls network connections DMZ, and the third one controls the internal network connections. In such a configuration it is usually DMZ and the internal network are hidden behind NAT (Network Address Translation).
One of key features DMZ is not only traffic filtering on the internal firewall, but also the requirement for mandatory strong cryptography in the interaction between active equipment of the internal network and DMZ. In particular, there should be no situation in which it is possible to process a request from the server in DMZ without authorization. If the DMZ is used to ensure the protection of information inside the perimeter from leakage from within, similar requirements are imposed for processing user requests from the internal network.