We use the commands sudo su. What is Sudo (su) Sudo s what does it mean
Sometimes, you just need to run a command from another user. And there are several ways how this can be done. I will talk about them in my article “Run a command as another user in Unix/Linux”.
Run a command as another user in Unix/Linux - method 1
And so, you can use the SUDO utility. Let's look at an example:
$ sudo -H -u Your_another_user -c "ping site"
Explanations:
- -H YOUR_HOME: Sets HOME (Environment variable for a specific user's home) and by default is root.
- -u YOUR_USER: Specify the user from whom the command will be executed.
- -c YOUR_COMMAND: Serves as an option to enter a command.
Something like this.
Run a command as another user in Unix/Linux - method 2
You can use the SU utility. And now I will give a few examples.
Login as root user
To get root, run:
$su - root
Run the command as root user
Here is an example command:
# su - root -c "YOUR_COMMAND_HERE"
Su - -c "YOUR_COMMAND_HERE arg1"
Execute a command from another user using su
So, here's an example:
# su -c "/opt/solr/bin/solr create -c test_solr_core -n solrconfig.xml" -s /bin/sh solr Created new core "test_solr_core"
Let's look at another example:
$ su another_user -c "ping site"
$su -YOUR_USER -c "YOUR_COMMAND_HERE"
- — — Will simulate the login of the specified user.
- -c - Used to specify the command to be executed (for the specified user).
Something like this.
Run a command as another user in Unix/Linux - method 3
And so, you can use the runuser utility. The runuser command starts a shell with replacement user and group IDs. This command is only useful when you are logged in as root. The syntax is as follows:
# runuser -l YOUR_USER -c "YOUR_COMMAND_HERE"
As an example, I'll show next line:
# runuser -l nginx -c "service nginx start"
PS: The runuser command does not require a password and should only be run by the root user.
Main options:
- -l: Create a login shell using the runuser-l PAM file instead of the default one.
- -g: Points to the main group.
- -G: Indicates an additional group.
- -c: Actually, it is used to specify a command.
- –session-command=COMMAND: Pass a single command to the shell with the “-c” option and does not create a new session.
- -m: Do not reset environment variables (ENVs).
That's it, the topic "Run a command as another user in Unix/Linux" is complete.
Separation of access rights is one of the most important security paradigms implemented in Linux and Unix-like operating systems. Regular users work with limited rights; This reduces their impact on their own environment and on the operating system as a whole.
The root user has superuser privileges. This administrator account does not have the restrictions that are present on regular user accounts. Other users can run commands with root rights in a number of individual cases.
This guide shows you how to properly and safely transfer root privileges to your system.
Note: This manual was performed on an Ubuntu 12.04 server, but most modern Linux distributions will behave in a similar way.
To complete the tutorial, you must first complete the initial server setup:
Login to the server as a non-root user.
How to get root rights
There are three main ways to gain superuser privileges, which vary in difficulty.
Login as root
The easiest way, of course, is to log in as root.
If connecting via SSH, provide the IP address or hostname:
ssh root@IP_address_or_domain
When prompted, enter your root password.
su command
It is not recommended to constantly use the root account, since, having absolute access rights, you can accidentally cause irreparable harm to the system.
Therefore, the system has the su command, which allows an ordinary user to obtain root rights at any time.
Note: The su command is short for substitute user.
So to root, just type:
The system will ask for the root user's password, after which it will open access to the root user's shell session.
After completing all tasks that require root rights, you can return to the previous session:
sudo command
The last way to gain root privileges is with the sudo command.
The sudo command allows you to run specific commands as root without having to open a new session.
sudo command_to_execute
Note: Unlike su, the sudo command does not ask for the root password, but rather the password of the user calling the command.
For security reasons, the sudo command is not available by default; access to it must be configured. If you've followed the initial server setup guide, you already know how to do this.
What is Visudo?
The sudo command is configured using the /etc/sudoers file.
Important! Never edit this file using a regular text editor! To do this you should use visudo.
Incorrect syntax added to this file can completely break the distribution of rights between users. Therefore, the visudo command is used to work with this file.
The visudo command opens the file normally text editor, but checks its syntax when saving the file. This avoids configuration errors.
Typically, visudo opens the /etc/sudoers file in the vi editor. On an Ubuntu system, visudo uses nano.
To configure the visudo command to use vi on an Ubuntu system, run the command:
sudo update-alternatives --config editor
There are 3 choices for the alternative editor (providing /usr/bin/editor).
Selection Path Priority Status
————————————————————
* 0 /bin/nano 40 auto mode
1 /bin/nano 40 manual mode
2 /usr/bin/vim.basic 30 manual mode
3 /usr/bin/vim.tiny 10 manual mode
Select the number corresponding to the text editor you want to use.
On CentOS, this value can be changed by adding the following line to ~/.bashrc:
export EDITOR=/path/to/editor
To update your settings, enter:
To open /etc/sudoers, enter:
Editing the sudoers file
So, in the text editor of your choice, the sudoers file will open on the screen.
Below are the Ubuntu 12.04 system file parameters (the commented lines are omitted and the changes made during the initial server setup are saved).
Note: The CentOS sudoers file is much larger; Some of its parameters are not described in this manual.
Defaults env_reset
Defaults secure_path="/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin"
root ALL=(ALL:ALL) ALL
demo ALL=(ALL:ALL) ALL
%admin ALL=(ALL) ALL
%sudo ALL=(ALL:ALL) ALL
Standard parameters
The first line, Defaults env_reset, resets the terminal environment to remove all user variables. This safety measure is used to eliminate potentially harmful exposure. environment variables from the sudo session.
The second parameter, Defaults secure_path=…, sets the path (PATH, dots file system, in which the OS will look for applications) for sudo operations. This prevents potentially dangerous user paths from being used.
User rights settings
The third and fourth parameters should be familiar to you. You added the fourth line yourself, but perhaps you did not examine it in detail.
- demo ALL=(ALL:ALL) ALL
- The first field specifies the username to which you want to apply this rule(in this case it's demo).
- The first ALL means that the rule will apply to all hosts.
- The second ALL means that the specified user can run commands in any user's session.
- The third ALL means that the specified user can run commands in any group.
- The last ALL indicates that these rules should be applied to all commands.
This means that root and demo users can run all commands using sudo with their password.
Group privilege settings
The last two lines are similar to the user privilege settings, but they are responsible for group rights.
Group names begin with the % symbol.
As you can see, the admin group can execute any command as any user or host. The sudo group has similar rights, but it can also run the command like any group.
Custom rules
Once you're familiar with the basic file syntax, try creating a couple of rules yourself.
Creating Aliases
The sudoers file can be more conveniently structured using various aliases.
For example, you can create three different user groups with combined rights:
User_Alias GROUPONE = abby, brent, carl
User_Alias GROUPTWO = brent, doris, eric,
User_Alias GROUPTHREE = doris, felicia, grant
Group names must begin with a capital letter. After this, you can give GROUPTWO users the right to change the apt-get database:
GROUPTWO ALL = /usr/bin/apt-get update
If the rule does not specify a user and group, sudo defaults to root.
You can then allow GROUPTHREE users to shutdown and restart the machine; To do this you need to create a command alias:
Cmnd_Alias POWER = /sbin/shutdown, /sbin/halt, /sbin/reboot, /sbin/restart
GROUPTHREE ALL = POWER
The POWER command alias contains commands for shutting down and restarting the machine.
You can also create an alias, Run as, which replaces the part of the rule that specifies the user in whose session the command should be executed.
Runas_Alias WEB = www-data, apache
GROUPONE ALL = (WEB) ALL
Now any user of the GROUPONE group can execute commands in www-data or apache user sessions.
Note Note: Remember that previously created rules take precedence in case of a rule conflict.
Blocking rules
There are a number of ways to control how sudo behaves and responds to calls.
For example, the updatedb command in combination with the mlocate package is relatively harmless. So that an ordinary user can perform it with superuser privileges without entering a password, you can create the following rule:
GROUPONE ALL = NOPASSWD: /usr/bin/updatedb
The NOPASSWD command means that the system will not prompt for a password. There is also a PASSWD command that does the opposite behavior and is used by default.
NOPASSWD applies to the entire rule unless the PASSWD command overrides it. For example, the line might look like this:
GROUPTWO ALL = NOPASSWD: /usr/bin/updatedb, PASSWD: /bin/kill
Another handy command is NOEXEC, which is used to prevent dangerous behavior of certain programs. For example, some commands, such as less, can call other commands:
This command executes any command with the privileges of the user running less, which can be very dangerous.
To prevent this behavior, you can use the following line:
username ALL = NOEXEC: /usr/bin/less
additional information
This section contains various useful tips on working with sudo.
If you specified a user or group in the Run as parameter, you can run commands in that user's session using the -u and –g flags, respectively:
sudo -u run_as_user command
sudo -g run_as_group command
By default, sudo stores credentials in one terminal for a period of time. This means that you will not have to enter your password again during this period.
If for security reasons you want to reset this timer, use the command:
To find out the user's rights, enter:
This command will list all permissions specified in the /etc/sudoers file for a given user.
If a normal user tries to run an administrator command without the sudo prefix, the command will not work. To avoid having to retype the command, use a bash function that repeats the command:
Double Exclamation point will repeat the last command.
Conclusion
You now have basic skills with the sudoers file and root permissions.
When working with superuser rights, remember that regular users do not have such rights by default for security reasons. Do not abuse root rights, otherwise you may accidentally cause irreparable damage to the system.
Tags: ,The sudo command is very important for managing access rights in operating system Linux. Thanks to this small command, you can grant permissions to perform certain actions on behalf of the administrator to other users, without giving them the superuser password itself. Also, you don't have to always sit under account superuser to occasionally perform administrative actions.
It would seem that such a small team, with a minimum of capabilities and maximum easy to use, but in reality she can do much more. In this article we will look at how sudo is configured in Linux to control access to system functions and user capabilities.
Before we move on to setting up access to the sudo utility, let's look at how it works. There are two ways to gain administrator rights in Linux. You can switch to the root user using the su command, or you can pass the desired command as a parameter to the sudo utility, which will execute it with administrator rights. Moreover, the second method is preferable, because you will not forget what you are using and will not do anything unnecessary.
The team name means substitute user do or super user do. The utility allows you to run programs as another user, but most often as the root user. The utility was developed back in 1980 by Bob Cogshell and Cliff Spencer. During this time, many developers have changed and many features have been added.
sudo works thanks to the SUID access flag. If this flag is set for a program, then it is executed not on behalf of the user who launched it, but on behalf of the owner, given that the file is owned by sudo, then the utility is executed as root. It then reads its settings, asks for the user's password, and decides whether the user can be allowed to run commands as an administrator. If yes, then the command passed in the parameter is executed.
Now that you know the theory, let's look at how to set up sudo on Linux.
Setting up sudo on Linux
All sudo settings are located in the /etc/sudores file. Here you can configure a lot of parameters, starting from who will be allowed to execute commands on behalf of the superuser and ending with limiting the set of available commands.
To open a file for editing, type the following command as superuser:
You can also specify the text editor in which you want to edit the configuration file:
EDITOR=nano visudo
Next we will look at the most interesting settings that you can set in this file. But first, let's look at the basic file syntax. It consists of two types of strings, these are aliases that allow you to create lists of users and flags, as well as the rules themselves, which specify how the sudo command will behave. The alias syntax looks like this:
type alias_name = element1, element2, element3
The type specifies what type of Alice should be created, the name is the name that will be used, and the list of elements specifies the elements that will be implied when referring to this name.
The description of user permissions has a slightly different syntax:
user host = (other_user:group) teams
The user specifies the user or group for which we are creating the rule, the host is the computer for which this rule will apply. Another user - under the guise of which user the first one can execute commands, and the last one can execute allowed commands. An alias can be used instead of any of the parameters. And now setting up sudo in Debian and other distributions.
Main settings
The Defaults alias allows you to specify standard parameters for the utility to work, we will consider them in this section. Such an alias begins with the word Defaults, followed by the name of the flag. If there is a ! symbol in front of the name, this means that the flag needs to be turned on; otherwise, turn it off:
Disable the introduction the first time you use it:
Defaults!lecture
The superuser cannot do sudo:
Defaults !root_sudo

Now if you try to run sudo sudo nothing will work:

Change the home directory for the target user, leaving the current user's folder as the home directory by default:
Defaults set_home

Save the list of groups of the current user:
Defaults !preserve_groups

Request superuser password instead of user password:


Set the number of password attempts before sudo quits, default is 3:
Defaults passwd_tries=5


The number of minutes that will pass before sudo asks for a password again is 5 by default. If you set the value to 0, it will always ask for a password, no matter how long ago you used the utility:
Defaults timestamp_timeout=10

The following parameter specifies the number of minutes that sudo will wait for a password to be retyped if it is entered incorrectly:
Defaults passwd_timeout=10

You can change the message that is displayed when prompted for a password:
Defaults passprompt="Your password:"

You can specify another user, not root, from which all commands will be executed, for this use:
Defaults runas_default="user"
You can log all attempts to connect to sudo:
Defaults logfile=/var/log/sudo

Then we try to check the operation of the log:
sudo cat /var/log/sudo

These were all the most interesting sudo settings that you may need, next we will look at how to set sudo access rights for users.
Setting up sudo users
We have already discussed above the syntax for setting up actions for users; here everything is more complicated than with aliases, but you can figure it out. For example, let's allow any user to use sudo, from any host, and execute any command:
ALL ALL = (ALL) ALL

Such a team is very unsafe; it allows everyone and everything. The first ALL is to allow all users, the second ALL is for all hosts, the third ALL is to allow login as any user, and the fourth is to allow any command to be executed. But another construction is used much more often:
%wheel ALL = (ALL) ALL

It means the same as the previous one, only here we do not allow all users to use sudo, but only those who are members of the wheel group.
%wheel ALL = (root) ALL
Here we have already limited the possible choice of users to only the root user. You can also specify the user group on behalf of which he can execute commands:
%wheel ALL = (root:admins) ALL

This means that you can run the command as root or another user from the admins group. We can also specify commands that the user can execute. For example:
%wheel ALL = (root) /bin/mount, /bin/umount

The user can only run the mount and umount commands as superuser. Now let's make it even more interesting, the user can execute mount and umount without a password, and all other commands with a password:
%wheel ALL = (root) ALL
%wheel ALL = (root) NOPASSWD: /bin/mount, /bin/umount
You can also restrict users by host, for example, allow using sudo only from host1:
%wheel host1 = (root) ALL
It remains to consider how to use aliases. Aliases can be of the following types:
- User_Alias- alias of users who will use sudo;
- Runas_Alias- alias of users on whose behalf commands will be executed;
- Host_Alias- host alias;
- Cmnd_Alias- command alias;
For example, let's create four aliases and use them in our rule:
User_Alias Users = user1,user2,user3
Runas_Alias Admins = root,admin
Host_Alias Hosts = host1,host2
Cmd_Alias Cmds = /bin/mount,/bin/umount
Users Hosts = (Admins) Cmds
This means that users from the Users list will be able to execute Cmds commands on behalf of Amdins users on Hosts hosts.
There are still a few words left to say about flags. The NOPASSWD flag tells you not to prompt for a password when executing this rule. For example, to allow all users to run the mount command with sudo without a password:
ALL ALL = (root) NOPASSWD: /bin/mount
You can also prevent this particular command from being executed at all using the NOEXEC flag:
ALL ALL = (root) NOEXEC /bin/mount
You can check whether the /etc/sudores file was configured correctly and see all the created rules using the command:
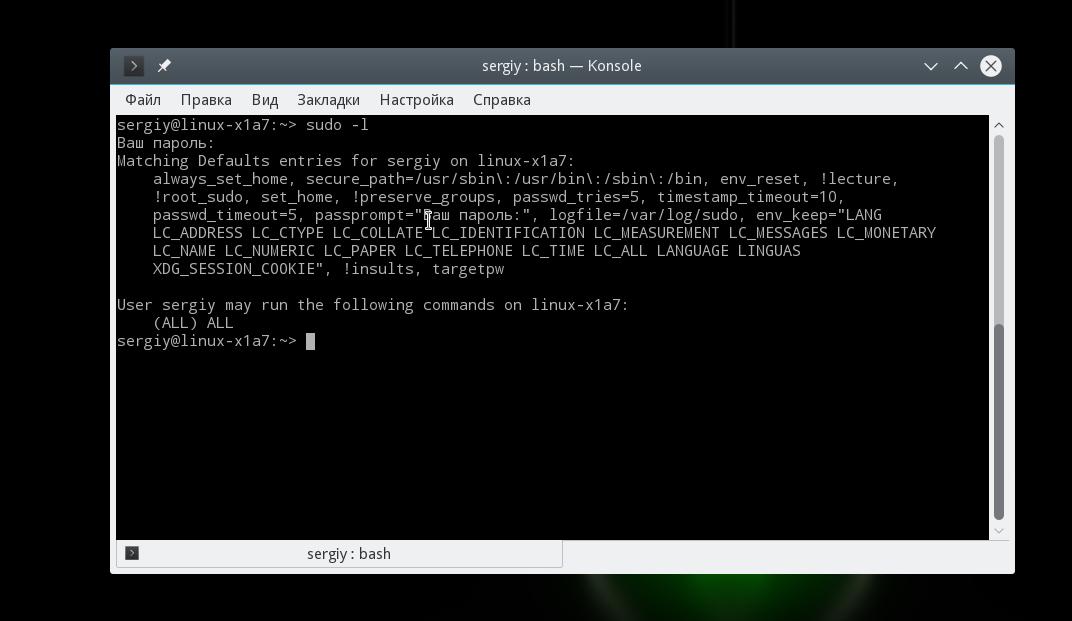
All installed flags and settings are displayed here, as well as the permissions of this user.
conclusions
In this article we looked at how to configure sudo in Linux. As you can see, despite the fact that this is very simple utility, she hides a lot useful settings, which you can use in your system. If you have any questions, ask in the comments!
A little about sudo itself, from Wikipedia. sudo(English) superuser do , literally “to perform on behalf of superuser") is a program designed to help system administrator and allowing you to delegate certain privileged resources to users while maintaining a log of work. The main idea is to give users as few rights as possible, but at the same time exactly as many as are necessary to solve the assigned tasks.
The sudo command allows users to run commands as root or other users. The rules that sudo uses to decide whether to grant access are in the /etc/sudoers file; The language of their writing and examples of use are described in detail in sudoers(5).
To edit the /etc/sudoers file, you should use the visudo program, which checks the syntax and thereby avoids errors in the rules.
In most cases, proper configuration of sudo makes running as superuser unnecessary.
By default, the root account in Ubuntu is disabled and root simply does not have a password. All administrative tasks are performed via sudo. By default, the right to execute sudo is granted to the first user created during installation. All others are regular users by default.
Sudo is a very flexible tool that allows you to configure rights to perform administrative actions for each user separately. For example, allow one to restart a server, and give another the ability to change access rights to files and folders. Open the /etc/sudoers file. This can be done either by issuing a command to open the file in your favorite text editor, for example like this:
# nano /etc/sudoers
or using the visudo utility:
# visudo
The latter method will open the /etc/sudoers file in the user's default editor, or if one is not specified, then in the vi editor. Advantage this method is that when saving the file will be checked for compliance with the syntax.
The simplest configuration looks like this:
Defaults env_reset
#User privilege specification
root ALL=(ALL) ALL
user ALL=(ALL) ALL
This configuration gives the user all the rights of the root user when running the sudo command. Defaults env_reset completely disables all user variables when executing commands as root. This is good from a security point of view, but sometimes causes problems. You can allow private variables to be used by a group or individual by adding a line like this:
Defaults:%admin !env_reset
which will save environment variables for all users of the admin group, or:
Defaults:user env_keep=TZ
which will save the TZ variable for the user user.
If the server is administered by a group of people, then it makes sense to do this:
%admin ALL=(ALL) ALL
As you might guess, this entry gives root access to all members of the admin group.
You can configure each specific user to have access to only specific commands. For example:
user ALL = /bin/mount, /bin/kill
will give user rights to execute mount and kill commands from any machine, and:
user2 mydebiancomp = /sbin/modprobe
will give user2 permissions to run modprobe from mydebiancomp. I think the syntax is clear:
user host = command
where the command is written with the full path. For a group, everything is similar, only the “%” sign is added.
III.Advanced sudo settings.
It is very convenient to create a group of aliases when setting up sudo. In order to avoid constantly repeating commands, users and hosts, we can group them into groups and set rules for each group of aliases. For example like this:
Cmnd_Alias command_alias = command1, command2, ... // command aliases
Host_Alias host_alias = hostname1, hostname2, ... // host aliases
User_Alias user_alias = user1, user2, ... // user aliases
Executing a command on behalf of another user is also possible. For example, with this entry:
user ALL = (user2, user3) /usr/bin/ark
user user can run the ark command as user2 or user3, using the u key, like this:
$ sudo -u user2 ark
By default, sudo remembers passwords for 5 minutes. If you do not want this, then for each user, group or alias you can set a separate rule, for example when:
Defaults:user timestamp_timeout=0
The user's password will not be remembered at all, but if:
Defaults:user timestamp_timeout=-1
will be remembered for the entire uptime.
Sudo without passwords is also possible. There is a similar design for this:
user myubuntucomp = NOPASSWD: /bin/kill
which will allow the user user from the host myubuntucomp to use kill without prompting for a password. Insert your own values, such as ALL instead of the hostname and command, so that the user can never enter a password to execute commands as root from any host, but remember that this makes the system very vulnerable.
Guard
Blogs, blogs, blogs. Maxim Fuckin knows a lot about this.
Interactive map of the city of Orenburg. Made using technology Google maps using our own developments. The resource is young, but already quite interesting and useful.